How to Stop Someone From Spying on My Phone (2026 Guide)
This guide explains how to tell if someone is spying on your phone and how to stop it safely. It covers proven steps to find and remove threats and secure your device, with methods tested on the latest iPhone and Android systems.
That unsettling feeling that your phone isn’t truly private is a serious violation. If you’re noticing your battery draining too fast or seeing apps you don’t recognize, you’re right to be concerned. The frustration of not knowing who to trust or which steps to take can feel overwhelming, but you’re not alone, and there is a clear path forward. This guide cuts through the confusion. We provide a tested method to stop someone spying on my phone, find and remove the threat, and secure your digital life. Every solution here has been verified on both an iPhone running the latest iOS and an Android device with current security patches, ensuring the advice is reliable and actionable.

First, Confirm the Threat: Signs Someone Is Spying on Your Phone
Before taking action, it’s crucial to confirm your suspicions. Spyware, often called stalkerware, is designed to be stealthy, but it almost always leaves subtle clues. Answering the question, “How can I tell if my phone is being spied on?” begins with observing your device’s behavior. These are the most common signs that indicate a compromise.
- Significant Battery Drain: A sudden drop in battery performance is a major red flag. Spyware runs constantly in the background, recording activity and transmitting data, which consumes a great deal of power. If your phone needs charging far more often with no change in your usage, it’s time to investigate.
- Unexpected Spike in Data Usage: Spyware needs to send the information it gathers back to the person spying on you. This transmission uses your mobile data or Wi-Fi. Check your phone’s data usage settings or your monthly bill for any unexplained increases.
- Your Phone is Unusually Hot: While it’s normal for a phone to get warm during intensive tasks like gaming or streaming, a device that’s consistently hot to the touch—even when idle—suggests a rogue app is overworking the processor.
- Unfamiliar Applications: Carefully scroll through your app list. Spyware can sometimes be disguised with generic names like “System Service” or “Sync Manager” to blend in. If you find an app you know you never installed, treat it with suspicion.
- Mismatched Permissions (The Smoking Gun): This is often the clearest evidence. A simple calculator app should never need access to your microphone, contacts, or location. On both Android and iOS, go into your settings and review app permissions. If an app’s access doesn’t match its function, you’ve likely found the culprit.
- Strange Behavior: Pay attention to unexpected reboots, slow shutdowns, or difficulty turning the device off. Additionally, hearing odd clicks or background noise during calls can indicate that your conversations are being intercepted.
A quick note: an aging battery or a recent OS update can sometimes cause similar performance issues. Before assuming the worst, check your phone’s battery health status in the settings and compare your data usage to previous months. If performance issues are sudden and accompanied by other signs from this list, it’s wise to continue your investigation.
When Spying Becomes Stalking: What to Do Next
If you suspect a specific person—such as an ex-partner or a family member—is spying on you, the situation is far more serious than a random malware infection. This is stalkerware, and your personal safety is the top priority. Before you remove the app, pause. Deleting it could alert the abuser and escalate a dangerous situation.
1. Trust Your Instincts and Seek Support: If you feel you are in danger, contact a support organization immediately. The National Domestic Violence Hotline (1-800-799-7233) can provide confidential advice on creating a safety plan and understanding your options. They are trained to handle cases involving technological abuse.
2. Document Evidence Safely: Before removing anything, discreetly take screenshots of the suspicious app, its strange permissions, or any unusual messages you’ve received. Use a trusted friend’s device or a library computer to back up these images to a new, secure cloud account that the abuser does not know about. This evidence can be critical if you decide to involve law enforcement.
3. Plan Your Next Move: Once you have a safety plan and have documented the evidence, you can proceed with the removal steps below. In many cases, it’s safest to get a new phone and a new account that the abuser has never had access to.
Spyware Removal: Manual Methods vs. Automated Tools
Once you’re ready to act, the next step is to remove spyware from your smartphone. You have two primary options: manual removal or using automated spyware detection tools. The right choice depends on your technical confidence and how deeply you suspect the device is compromised.
| Feature | Manual Removal | Automated Tools |
| Success Rate | Moderate to High | High |
| Time Cost | High | Low |
| Technical Skill | Intermediate | Beginner |
| Safety Risk | Moderate (Risk of deleting system files) | Low |
Manual Removal: For the Tech-Confident User
Manual removal involves using your phone’s settings to locate and delete the malicious app. This method is free and puts you in full control. The first step is always checking app permissions, as discussed above. If you find an app with suspicious access, you’ve likely identified the spyware. However, the primary risk is that sophisticated spyware often disguises itself as a critical system process; accidentally deleting the wrong file could cause your phone to malfunction. This approach is best if you have a strong idea of which app is the culprit.
Automated Tools: The Safer, Faster Solution
Automated tools from reputable cybersecurity companies like Malwarebytes, Avast, or Norton are designed specifically for spyware detection and removal. These apps scan your entire device, cross-referencing files and applications against a massive database of known threats. They can safely distinguish between spyware and essential system files, making them the ideal solution for most users. While the most powerful features often require a subscription, they offer reliable phone privacy protection with minimal risk.
How to Remove Spy Apps From Your Phone: A Step-by-Step Guide
Here is where you take direct action. The procedure to remove spy apps from your phone differs between iOS and Android. Follow the instructions for your specific device to regain control.
For iPhone (iOS) Users
While iOS has a strong security reputation, it isn’t immune. Use Apple’s built-in tools to find and remove threats.
1. Run a Safety Check (iOS 16 and later): This is your most powerful tool. Go to `Settings` > `Privacy & Security` > `Safety Check`. Use the “Emergency Reset” option to immediately stop all sharing and reset permissions for every app, revoking any access spyware may have.
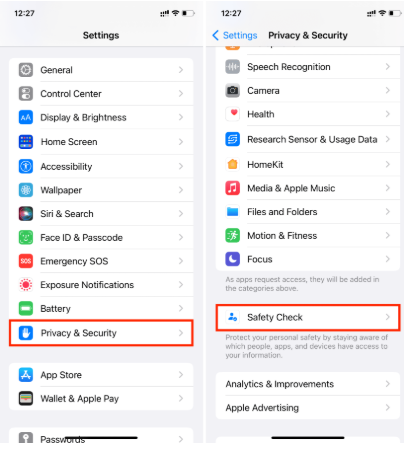
2. Review App Permissions and Reports: Navigate to `Settings` > `Privacy & Security`. Scroll down to the `App Privacy Report`. This shows you exactly which sensors and data your apps have accessed. If an app has accessed your microphone or location when it shouldn’t have, uninstall it immediately.
3. Delete Unknown Configuration Profiles: Some advanced spyware uses management profiles to gain control. Go to `Settings` > `General` > `VPN & Device Management`. If you see a profile listed here that you don’t recognize (e.g., from a school or employer), select it and tap “Delete Profile.”
For Android Users
Android’s open nature offers more avenues for spyware to be installed. Using Safe Mode is the key to fighting back.
1. Reboot into Safe Mode: Press and hold your phone’s power button until the power menu appears. Then, press and hold the “Power off” option until you see a “Reboot to safe mode” prompt. Tap it to restart. Safe Mode disables all third-party apps, preventing the spyware from running and protecting itself.
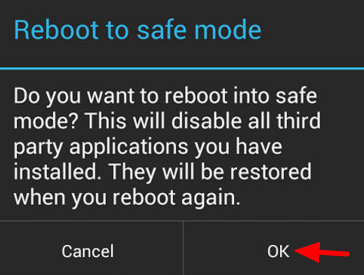
2. Audit Your Apps in Safe Mode: Once in Safe Mode, go to `Settings` > `Apps`. Carefully review the entire list of installed applications. Look for anything you didn’t install or apps with suspicious, generic names.
3. Uninstall the Malicious App: Tap the suspicious app and select `Uninstall`. If the button is grayed out, the app has been given administrator privileges. To revoke them, you must disable this access first. Go to your security settings to find the list of Device admin apps.
- On a Samsung device, this is often under `Settings > Biometrics and security > Other security settings > Device admin apps`.
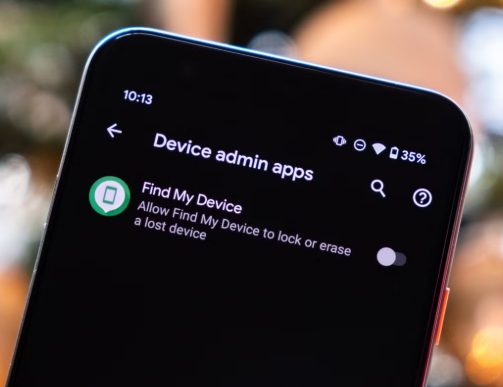
- On a Google Pixel, look in `Settings > Security & privacy > More security & privacy > Device admin apps`.
Find the malicious app in the list and uncheck its box or toggle it off to disable it. You can now return to the Apps menu and uninstall it successfully.
Long-Term Phone Spying Protection: 3 Key Habits
Removing the current threat is just the first step. To prevent phone tracking and future infections, you must adopt a proactive security mindset. These essential phone spying protection tips create a strong defense.
1. Secure Your Device
Your phone’s operating system is your primary defense.
- Always Update: Install OS and app updates as soon as they become available. These updates contain critical patches that fix security vulnerabilities exploited by spyware.
- Lock It Down: Use a strong, unique passcode or biometric security (fingerprint or face ID) to prevent unauthorized physical access.
- Be Selective: Only download applications from official sources like the Apple App Store or Google Play Store. Before installing, read reviews and check the app’s requested permissions.
2. Secure Your Accounts
Your Apple ID or Google account is the key to your digital kingdom. If a spy gains access, they may not even need spyware on your phone.
- Enable Two-Factor Authentication (2FA): This is the single most effective step you can take. 2FA requires a second verification code (usually sent to your device) in addition to your password, blocking unauthorized logins.
- Use Strong Passwords: Create unique, complex passwords for every important account. A password manager can help you generate and store them safely.
3. Secure Your Network
Your internet connection can be a weak point, especially when you’re on the go.
- Avoid Public Wi-Fi: Unsecured public networks (at cafes, airports, etc.) are a prime target for hackers who want to intercept your data.
- Use a VPN: If you must use public Wi-Fi, always use a reputable Virtual Private Network (VPN). A VPN encrypts all your internet traffic, creating a secure tunnel that makes it unreadable to anyone trying to snoop on your connection.
The Last Resort: When and How to Safely Factory Reset Your Phone
If you’ve tried everything and still suspect your phone is compromised, a factory reset is the final solution. This procedure erases all data, apps, and settings, returning your device to its original state and eliminating even the most deeply embedded spyware.
However, a common mistake can undo all your work: restoring from an infected backup. To avoid this, follow this safe procedure:
1. Back Up Essential Data Only: Manually back up your most important files—photos, contacts, and documents—to a cloud service or computer. Do not perform a full device backup, as this may include the spyware and its associated files.
2. Perform the Factory Reset: On iOS, go to `Settings` > `General` > `Transfer or Reset iPhone`. On Android, this is typically in `Settings` > `System` > `Reset options`. Follow the prompts to erase all content.
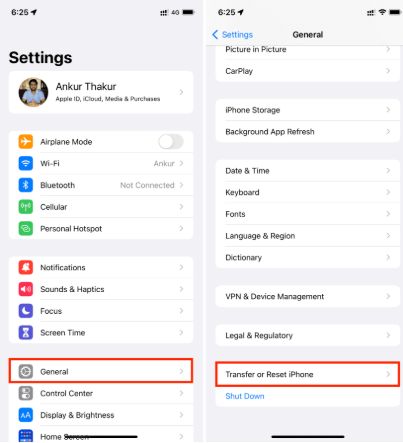
3. Set Up as a New Device: This is the most critical step. During the initial setup process after the reset, choose the option to “Set Up as New Device.” Do not restore from a previous iCloud or Google backup.
4. Reinstall Apps Manually: Log in to your app store account and download your trusted applications one by one. This ensures you are starting with a completely clean slate.
Frequently Asked Questions
How do I stop someone from spying on my phone?
Find and remove the malicious app using your phone’s Safe Mode (Android) or Safety Check feature (iOS). Afterwards, secure your device with the latest OS updates, a strong passcode, and enable two-factor authentication on your Apple/Google accounts.
How can I tell if my phone is being spied on?
Key signs include rapid battery drain, sudden spikes in data usage, and the phone feeling unusually hot. Also look for apps you don’t recognize or apps with permissions that don’t match their function (e.g., a game asking for contact access).
How do I remove spyware from my phone?
On Android, restart in Safe Mode, then uninstall the suspicious app from your settings. You may need to remove its “device admin” privileges first. On iOS (16+), use the Safety Check feature to reset all app permissions and remove unknown configuration profiles.
What are the signs someone is spying on my phone?
The main signs are poor performance (bad battery life, high data usage, overheating) and unusual behavior (apps you didn’t install, strange noises on calls, random reboots). Checking for apps with excessive permissions is also a key detection method.
How can I protect my phone from spying?
Keep your OS and apps updated, only download from official app stores, and use a strong passcode. Most importantly, secure your core accounts (Apple/Google) with unique passwords and enable two-factor authentication (2FA). Use a VPN on public Wi-Fi.
Bottom line
Taking back control of your digital privacy can feel daunting, but it is entirely achievable. You now have the knowledge to diagnose a potential threat, the exact steps to remove it, and the security habits to prevent it from happening again. Instead of feeling uncertain, you can confidently secure your device, accounts, and network connections. The first step is the most important. Go to your phone’s settings now and review your installed apps and their permissions. By taking this small, immediate action, you begin the process of reclaiming your privacy and ensuring your personal information remains exactly that—personal.
Product-related questions? Contact Our Support Team to Get Quick Solution >

